VPN Comprehensive Guide to Secure Online Privacy
Recently began using a VPN to protect my online activities. I sometimes type “VNP” by mistake, which reminds me to check my spelling. In this article, I explain how a VPN works and why it matters.
Table of Contents
Understanding VPN
A VPN is a tool that secures your internet connection. It hides your IP address. It encrypts your data. I use a VPN every day to safeguard my online privacy. Moreover, a VPN prevents tracking by websites and hackers.
Why Use a VPN?
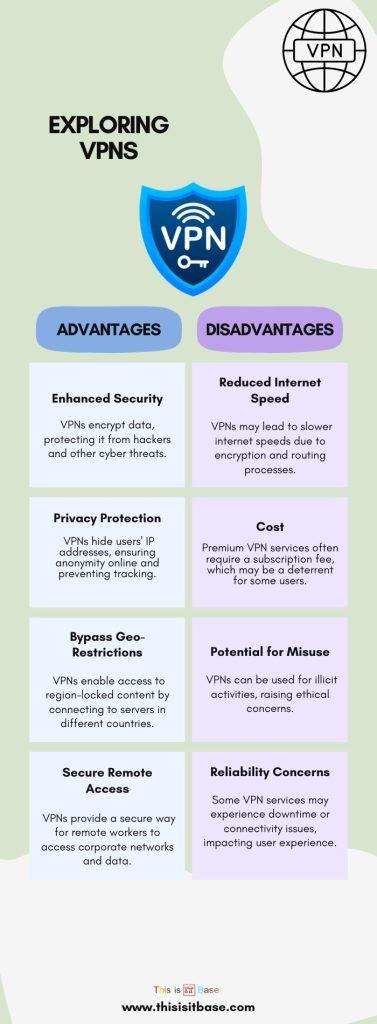
A VPN offers many benefits. It keeps your information safe. It improves your browsing privacy. I appreciate its role in accessing geo-restricted content. Additionally, a VPN’s lets you work remotely with confidence.
- Security: It shields your data from cyber threats.
- Privacy: It masks your digital identity.
- Freedom: It lets you access global content.
- Convenience: It works on multiple devices seamlessly.
These benefits have made my online experience more secure and flexible.
Comparing Top VPN Providers
Below is a table that compares some popular VPN’s services. This guide helps you decide which option suits your needs.
| VPN Provider | Price | Key Features | User Rating |
|---|---|---|---|
| ExpressVPN | $8.32/month | Fast speeds, strong encryption | 4.8/5 |
| NordVPN | $3.71/month | Large network, robust security | 4.7/5 |
| CyberGhost | $2.25/month | User-friendly, streaming support | 4.5/5 |
| Surfshark | $2.49/month | Unlimited devices, budget-friendly | 4.6/5 |
I compare these providers often. Transition words like “moreover” and “furthermore” help me explain the differences.
My Personal Experience with a VPN
I started using a VPN’s after noticing unusual ads and slow connection speeds. My internet felt unsafe. Installed a VPN’s, and started then browsing speed improved. I love that it secures my personal data when I work on public Wi-Fi. I even corrected my typo “VNP” during setup. These small mistakes remind me to pay attention to details.
Using a VPN has opened new possibilities. I now access global content without restrictions. I feel more secure and confident online. The VPN’s I use makes my workflow smooth, especially during video calls and remote work sessions.
Tips for Choosing the Right VPN
If you want to select a VPN that fits your needs, consider these tips:
- Check the Price: Look for competitive rates that offer value.
- Review Features: Ensure it supports encryption, multiple devices, and fast speeds.
- Read Reviews: User feedback helps guide your choice.
- Test the Service: Use free trials to verify performance.
- Consider Customer Support: Choose providers with reliable service.
These tips have helped me avoid poor-performing services. I now choose a VPN’s with confidence.
Conclusion
A VPN’s is essential for protecting your digital life. It provides security, privacy, and access to global content. My experience shows that using a VPN’s improves online safety and performance. I encourage you to explore VPN’s options and find one that meets your requirements. Enjoy the benefits of secure online privacy, and always remember to double-check your typing to avoid mistakes like “VNP.”
Infographic: Exploring VPNs: Advantages and Disadvantages